Exploiting XXE in File Upload Functionality
Blackhat USA - 2015
Will Vandevanter - @_will_is_
Agenda (25 minutes):
- OOXML Intro
- XML Entity Examples
- Further Exploitation
Corrected Slides, References, and Code:
oxmlxxe.github.io
Office Open XML (OpenXML; OOXML; OXML)
- *.docx, *.pptx, *.xlsx
- "Open" File Format developed by Microsoft
- Available for Office 2003, Default in Office 2007
- ZIP archive containing XML and media files

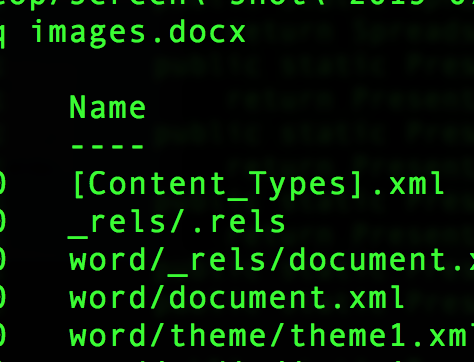
General Parsing OOXML
- /_rels/.rels
- [Content_Types].xml
- Default Main Document Part
- /word/document.xml
- /ppt/presentation.xml
- /xl/workbook.xml






Bug Bounty: Slack.com
- File Sharing Functionality
- [Content_Types].xml
Bug Bounty: Facebook Careers
- Q4 2014 - Mohamed Ramadan
- Resume Upload Functionality
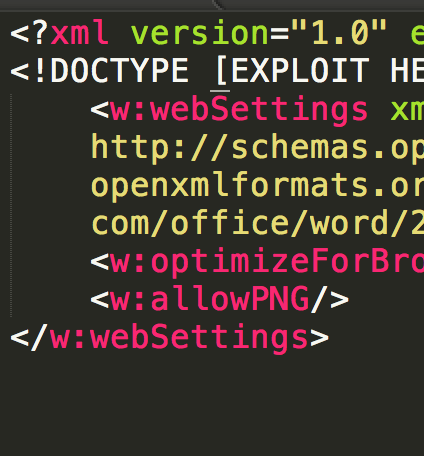
oxml_xxe demo
External DTD PoC
XML Entity
< !DOCTYPE root [
< !ENTITY post "MYSTRING">
]>
DOCX
/word/document.xml
PPTX
/ppt/presentation.xml
XLSX
/xl/workbook.xml
Recursive XML Entity
< !DOCTYPE foo [
< !ENTITY post "1">
< !ENTITY post1 "&post;&post;">
< !ENTITY post2 "&post1;&post1;">
< !ENTITY post3 "&post2;&post2;">
< !ENTITY post4 "&post3;&post3;">
< !ENTITY post5 "&post4;&post4;">
]>
< foo> &post5; < /foo>
Recursive XML Entity
Apache POI
CVE-2014-3574
CVE-2014-3529
docx4j
OpenXML SDK
Nokogiri
CVE-2012-6685 (ish)
CVE-2014-3660
+OXML_XXE
XSS Testing
LFI
Relationship Id="rId1" Type="...relationships/officeDocument" Target="/word/document.xml"
Other File Formats
+OXML Features
hlinkHover
XSLTransform
Embedded "Documents"
SSRF
+Testing Cheatsheet
Classic (X)XE in OXML
Canary Testing DTD and XE
XSS XE testing (CDATA/plain/attr)
XE LFI
Embedded (X)XE attacks
SSRF (X)XE
"Save As" Document Conversion
Summary Points
(DEFENSE) The libraries that parse XML on one part of the site (e.g. API) may not be the same ones that parse uploaded files; verify! Check configurations.
(DEFENSE) Patches exist, many are recent
(OFFENSE) Lots of surface area for exploitation
(OFFENSE) Untouched research targets
Questions?
http://oxmlxxe.github.io